Product Security
We design our products with cybersecurity at their core.

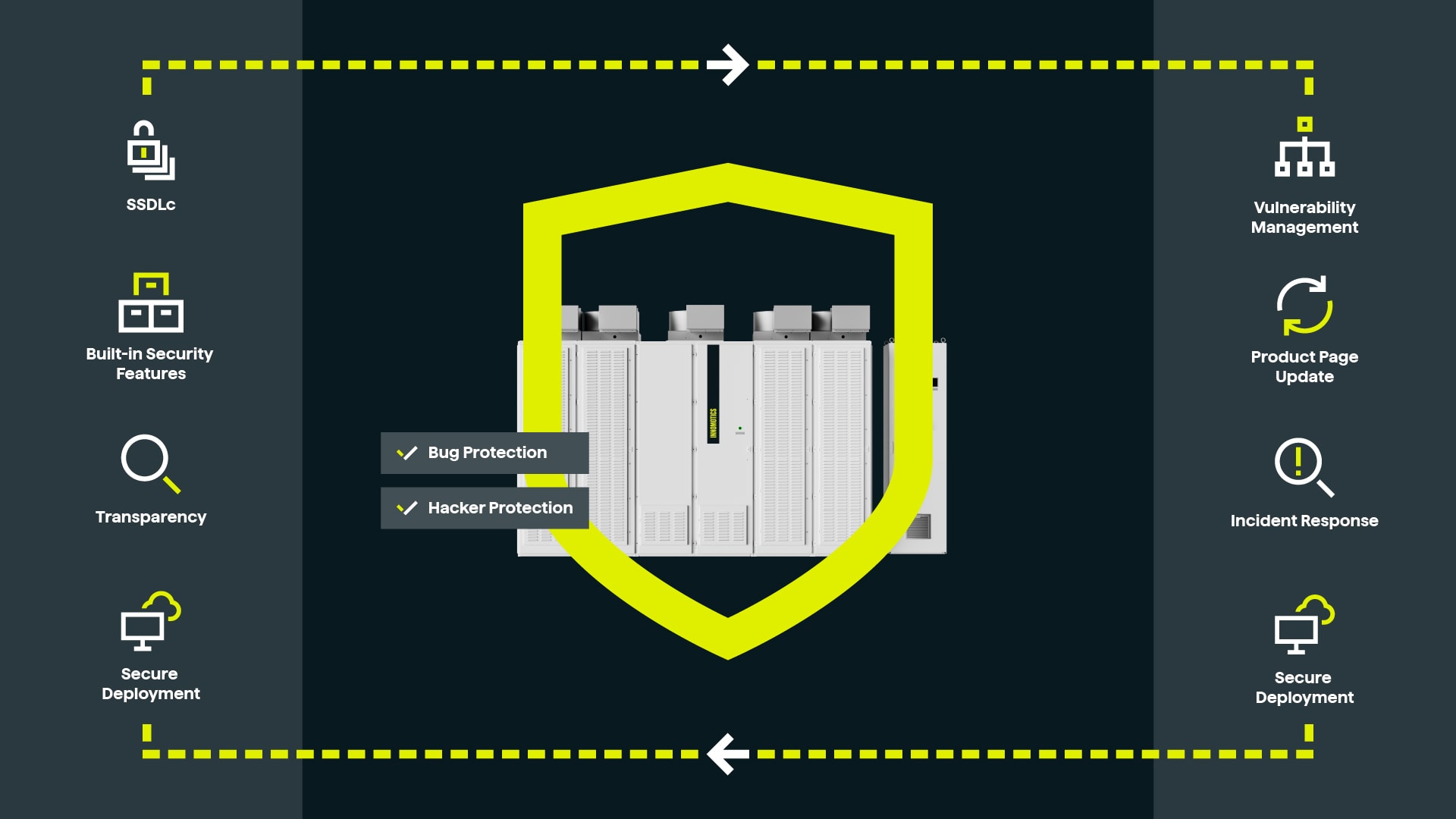
Protect your operations with built-in cybersecurity.
Product security is essential because our products support critical processes across industries that impact both your business and society. As industrial systems become more connected and dependent on digital communication, the risk of cyberattacks increases. Such attacks can disrupt operations, damage system integrity, and affect your business performance. Recognizing this risk, we are committed to cybersecurity by embedding security measures into our products and processes. This approach ensures cyber-resilient solutions that comply with leading international standards such as IEC 62443, helping to protect your operations effectively.
Secure Product Development Lifecycle
We build security in from day one — across our Drives, digital portfolios, and related solutions. This approach helps reduce risks and gives you confidence in our products.
Key steps like threat assessments, code reviews, and automation keep us ahead of evolving cyber challenges. Our DevOps and security teams work hand in hand to strengthen protection at every stage. From development to incident and vulnerability management, this lifecycle makes sure our products stay resilient against cyber threats over the long haul.
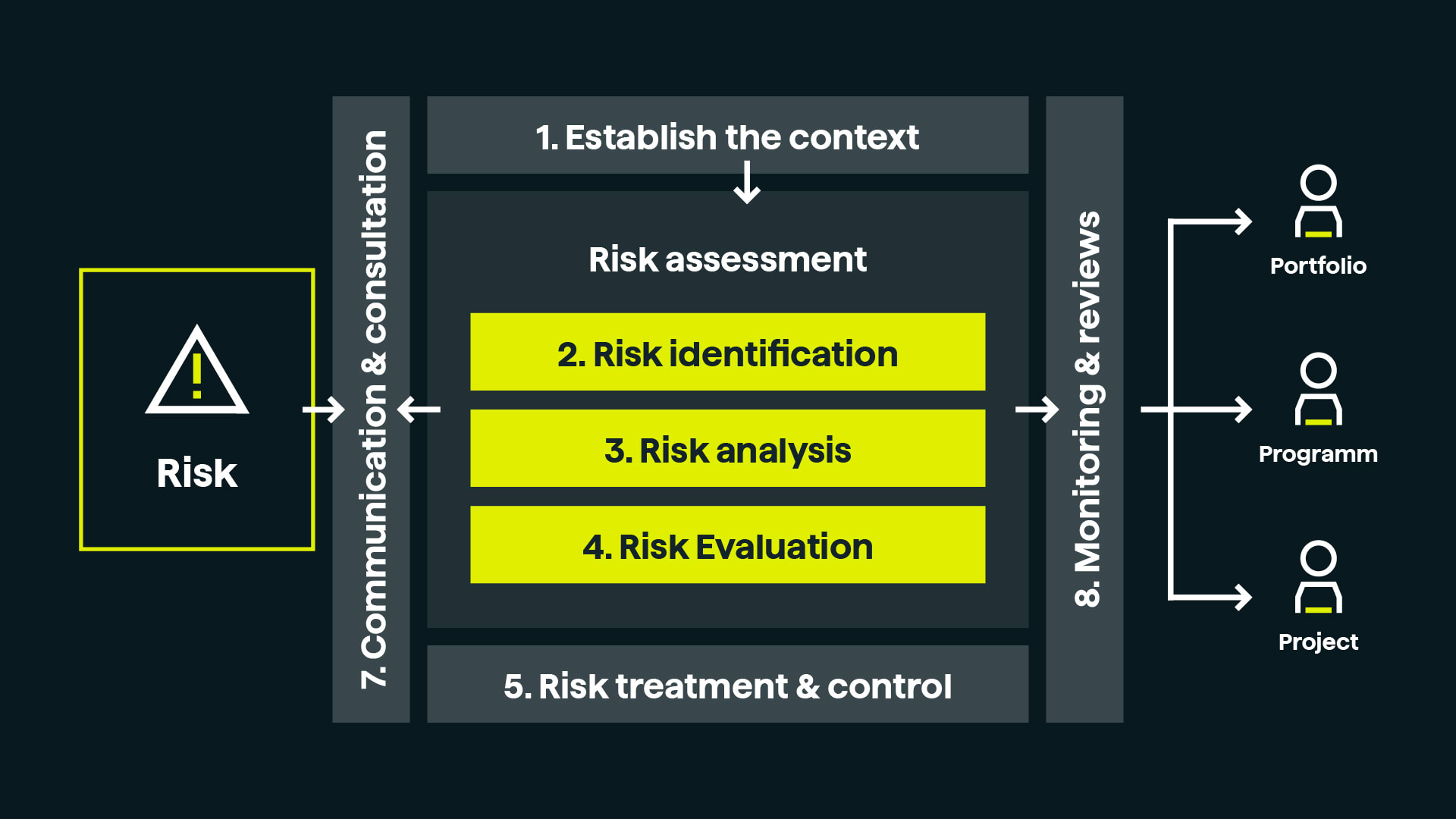
Committed to cybersecurity you can trust
We’re dedicated to top-level cybersecurity for every product with digital elements. We follow regulations like the EU Cyber Resilience Act (CRA) closely — from planning and design through development, production, delivery, and maintenance.
We conduct thorough risk assessments. They’re carefully documented, updated regularly, and integrated into all technical documentation. Our process quickly finds, records, and fixes vulnerabilities to match each product’s risk profile.
If serious issues arise, we inform you transparently and provide timely guidance to keep you safe. Sometimes, we delay public disclosure of fixes so you can apply patches first and stay protected.
We also anticipate risks from intended use or potential misuse — so you can rely on our products with confidence.
Your security is our priority.
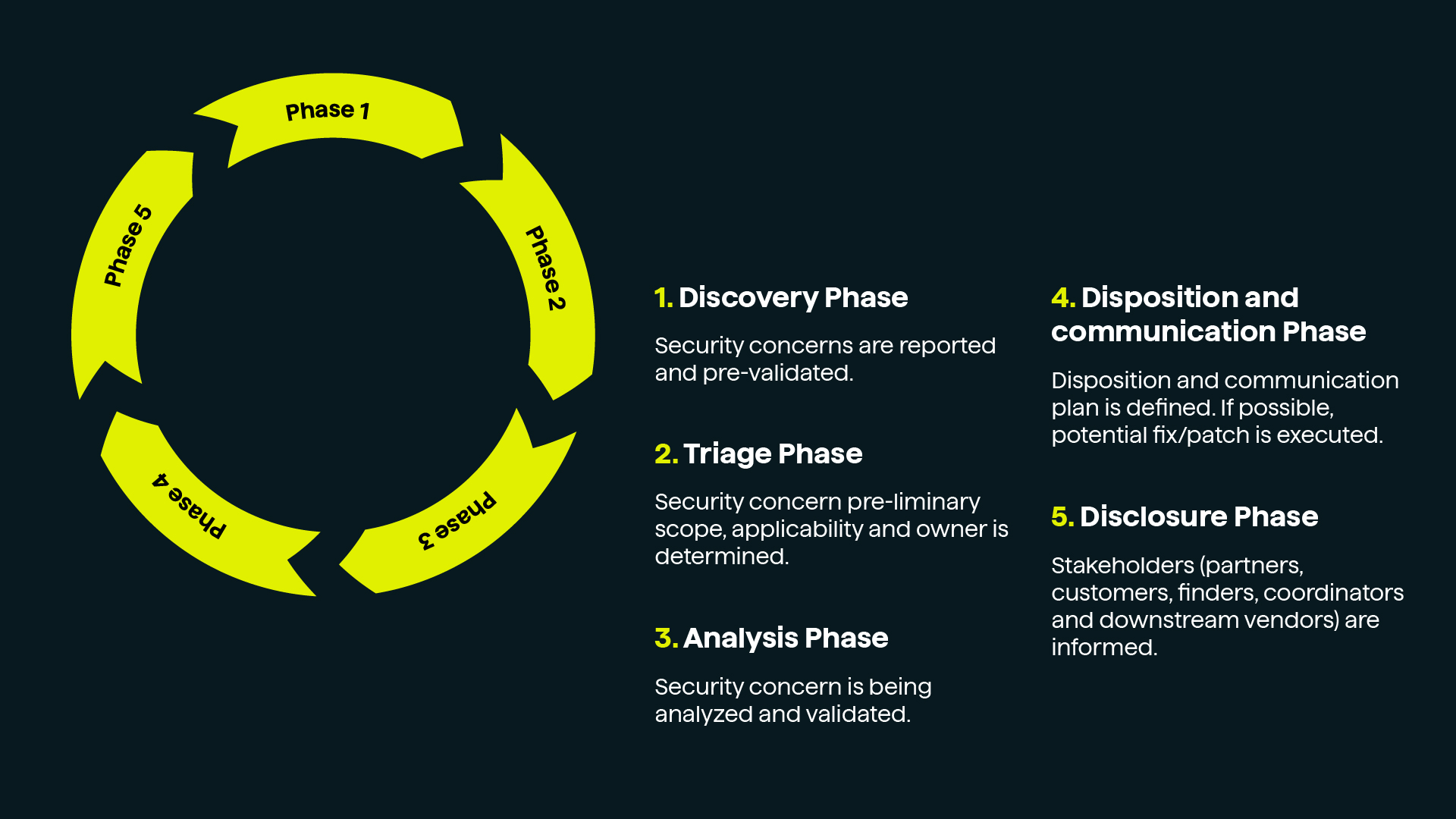
Vulnerability management
Comprehensive vulnerability management is essential to protect our products and ensure their reliability. Fully aligned with the Cyber Resilience Act (CRA), we monitor, assess, and mitigate risks throughout the entire product lifecycle — boosting cyber resilience and meeting global standards.
We act quickly on valid vulnerabilities and recommend coordinated disclosure to block zero-day threats and keep you safe. In line with CRA, we notify the designated CSIRT coordinator and ENISA via the single reporting platform about actively exploited vulnerabilities and severe incidents — issuing early warnings within 24 hours and full reports within 72 hours.
Got a vulnerability to report? Contact us at SVM@innomotics.com. You’ll also find our full coordinated vulnerability disclosure policy there.
Coordinated vulnerability disclosure
- Everyone is encouraged to report vulnerabilities — regardless of product age or service contract.
- We welcome reports from all sources, including researchers, CERTs, partners, and others.
- We respect reporters’ preferences, including anonymous submissions.
- We commit to addressing valid vulnerabilities related to our products.
- We recommend coordinated disclosure to avoid exposing customers to unpatched risks.
- Publicly disclosing too soon can create zero-day threats, so we urge cooperation to keep systems secure.

Transparency & security assurance
We provide essential security insights upfront to ensure there are no surprises after deployment. Contact your local sales representative for:
- Product whitepaper – a detailed overview of built-in security features
- SBOM (Software Bill of Materials) – a comprehensive list of software components
- Cybersecurity advisory – expert guidance on security best practices
- Secure configuration guidelines – recommendations for a safeguarded environment
- MDS2 statement – manufacturer’s security disclosure

Built-in security controls for our next-generation products
Our latest generation products come with essential security controls to keep your systems safe and reliable. These include:
- Secure configuration and hardening
- Authentication and authorization
- Whitelisting
- Data encryption
- Trusted machine certificates
- Auditing and logging
Incident reporting and response

At Innomotics, we’re committed to addressing cybersecurity incidents quickly and effectively. Reporting incidents immediately is crucial for fast containment and resolution.
- Report: Submit your report to our incident management team.
- Evaluate: Our team assesses incidents 24/7.
- Analyze: Forensic analysis identifies the cause.
- Restore: We help restore systems to full functionality. To report an incident, please contact us at productcert@innomotics.com.
Inspire IQ with secure cloud service
Our digital platform optimizes the performance and efficiency of industrial drive systems through real-time monitoring, predictive maintenance, and cloud-based data analysis. It also features robust cloud security to safeguard your data, ensuring all transmitted and stored information stays protected.
With this integration, you can improve productivity, reduce downtime, and make data-driven decisions with confidence.
For more information, visit our Innomotics Inspire IQ Webpage.
Cybersecurity alerts and notification
We’re committed to providing our customers with products, systems, and services that clearly address cybersecurity. Our approach ensures you receive timely alerts and transparent notifications about potential risks and vulnerabilities. This helps you stay informed and protected at all times.
Please visit the Innomotics Security Advisories for more information.