Cybersecurity
Preserving value, securing trust

Cybersecurity in motion.
Keeping your operations safe, secure, and moving forward.
Cybersecurity isn’t optional — it’s essential. In today’s connected industrial world, cyber threats can shut down your production, put safety at risk, and disrupt your entire supply chain. That’s why we build cybersecurity into everything we do. We secure our operations, our products, and offer solutions that protect yours. Together, we prevent attacks, protect critical infrastructure, and keep you compliant. Because when your operations stay in motion, so does your business.
Our focus
- Maintain a leading cybersecurity posture
- Build trust with our partners and suppliers
- Partner with leading cybersecurity providers to deliver effective security
- Maximize efficiency
Our focus areas
Our cyber defense coverage extends across both information technology (IT) security and industrial security, ensuring comprehensive protection for your entire operation.




Security, layer by layer.
Our defense-in-depth approach keeps your systems protected — from the inside out.
We don’t rely on a single line of defense, and neither should you. We add multiple layers of protection to secure your infrastructure at every level. We control physical access to critical components. We enable secure communication across your industrial networks to block unauthorized access. We shield your automation systems and control components from manipulation and malware — so your operations stay safe, stable, and in motion.
Built-in security for our products, every step of the way.
We build security into everything from day one. Our products are developed using secure-by-design principles to minimize vulnerabilities from the start. We watch for emerging cyber threats and act fast. With proactive monitoring and timely updates, we address vulnerabilities as they appear — keeping your systems protected and running smoothly.
Comprehensive concept as recommended by IEC 62443
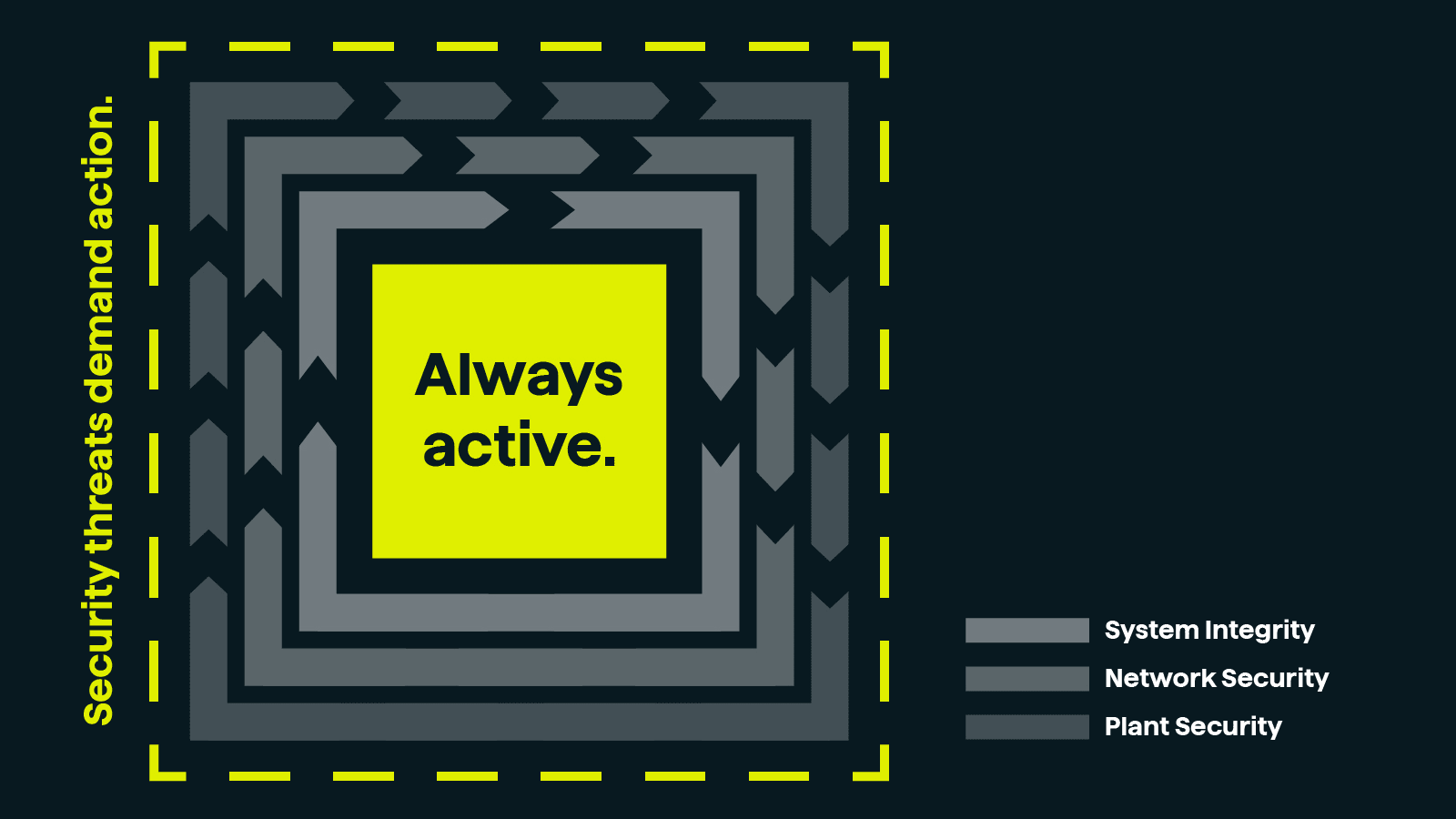
At Innomotics, our Defense-in-Depth concept provides a multilayer security approach that ensures holistic and in-depth protection for your plant. This approach aligns with the International Electrotechnical Commission's IEC 62443 standard.
Our multilayer security includes:
- Plant security protection and security management specifically designed for automation systems
- Network security that ensures secure communication within industrial networks
- System integrity measures to safeguard automation systems and control components

Publications
We regularly publish security advisories and bulletins to keep you up to date on validated vulnerabilities affecting our offerings. When action is needed, we inform you — whether that means installing an update, performing an upgrade, or taking other steps to keep your systems secure. Please visit the Innomotics Security Advisories for more information.
Proactive threat protection.
We take a proactive approach to security with our dedicated Cyber Emergency Response Team (CERT). They quickly address emerging threats and issue timely security advisories to keep you informed and protected.
Cyber risk management.
Our cybersecurity risk management framework protects your critical assets by actively managing cyber risks. Aligned with ISO 27005 and industry best practices, we continuously monitor, communicate, and mitigate risks to support your business goals and ensure long-term security.
Trust and certification
Committed to global compliance and excellence, we at Innomotics hold independent certification under ISO/IEC 27001:2022.
This demonstrates our serious commitment to protecting data privacy and cybersecurity — not just for today, but for the long-term success of your business and everyone who depends on it. As your trusted partner in operations and supporting your operational journey, we aim to give you every reason to place your confidence in Innomotics.
Our global Cybersecurity Management System covers both information security and privacy information management. Our central cybersecurity teams at our Nuremberg headquarters lead governance and assurance, keeping our defenses strong worldwide.
Data privacy
We take the protection of your data very seriously. To support your compliance with the GDPR regulations in Europe, our processes follow the fundamental principle of "privacy by design and by default." This means data protection is built into our products, solutions, and services right from the initial design and planning stages.


